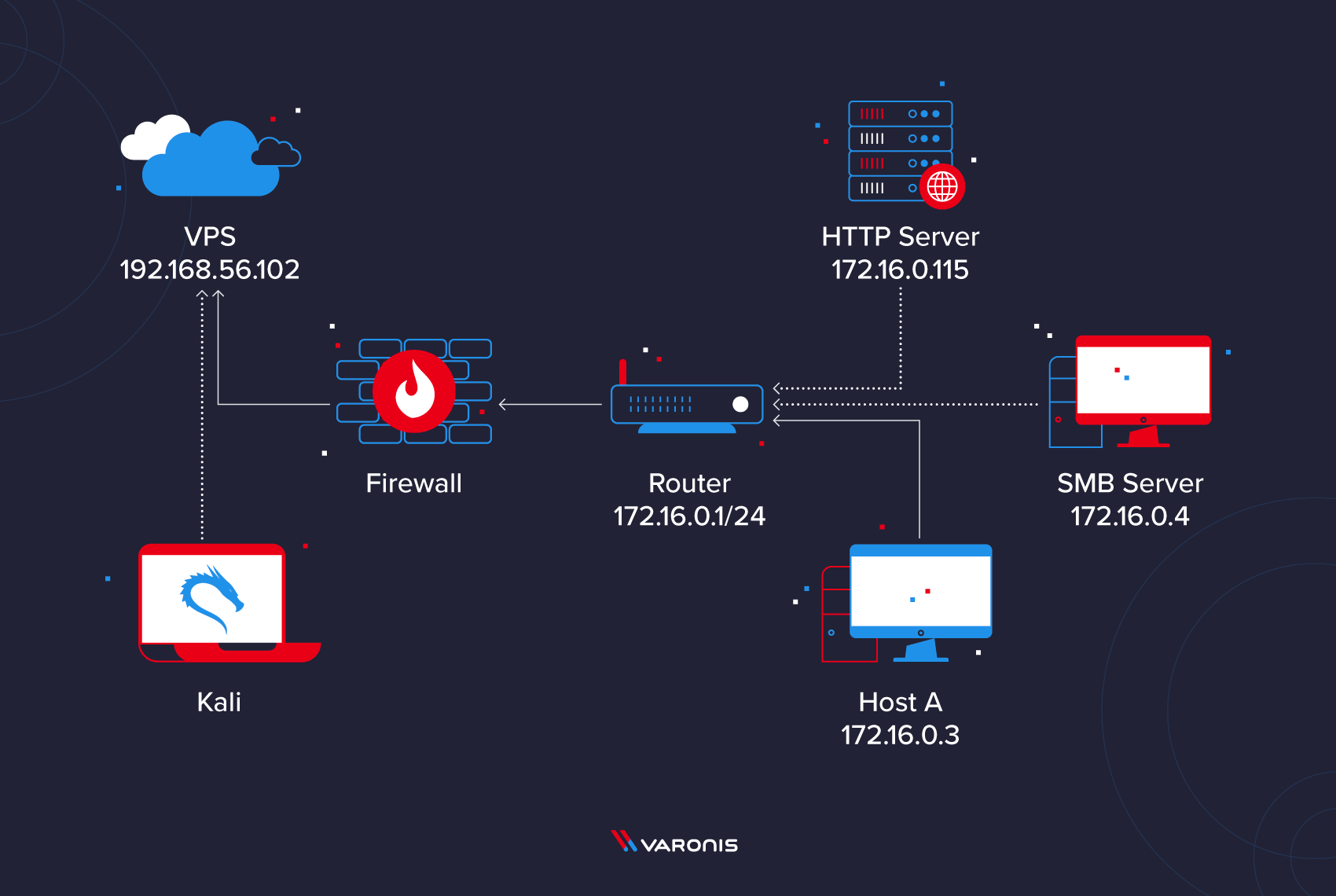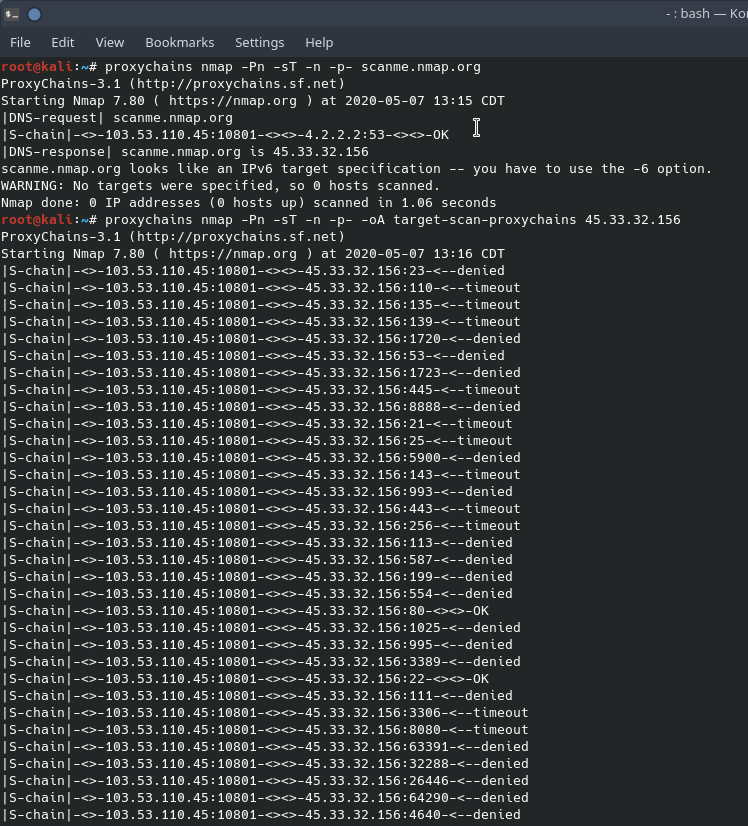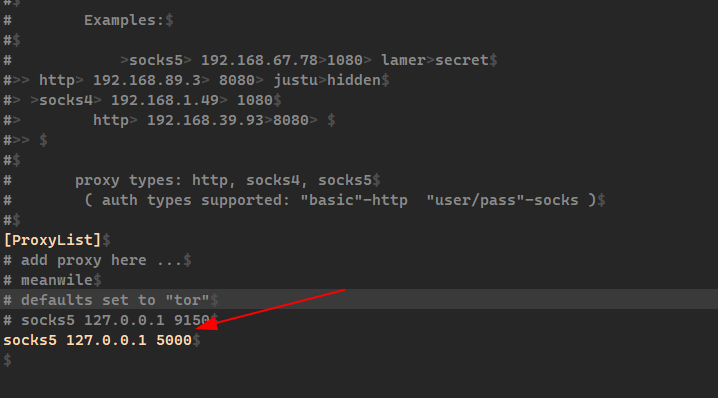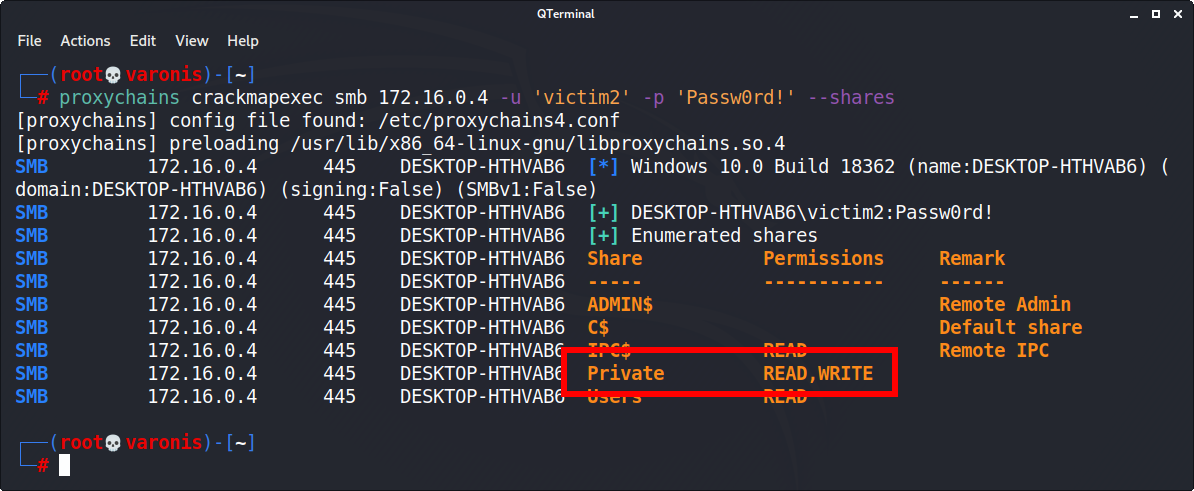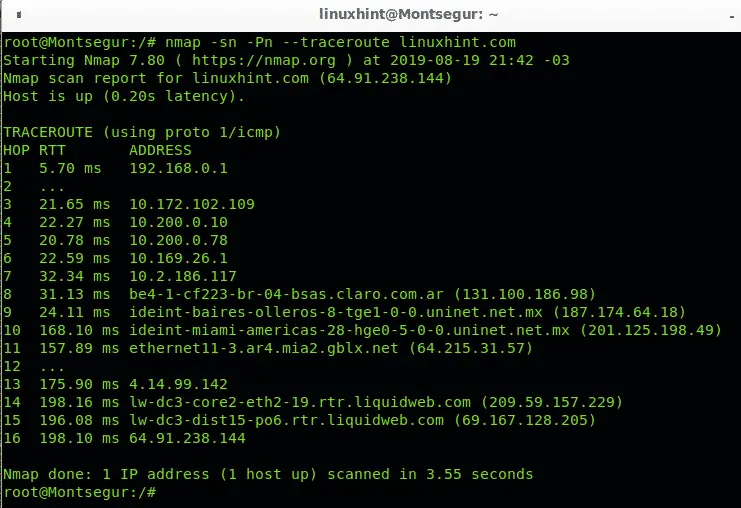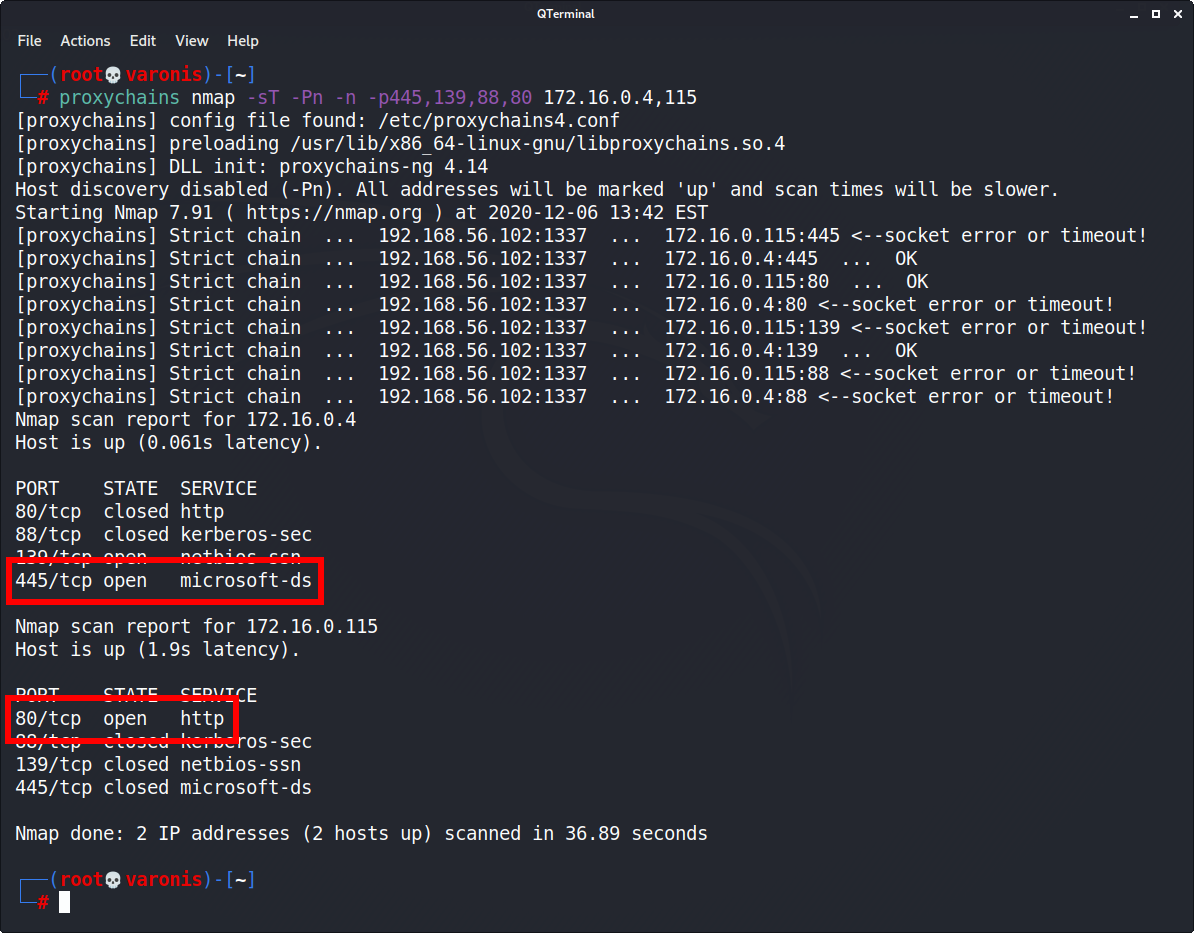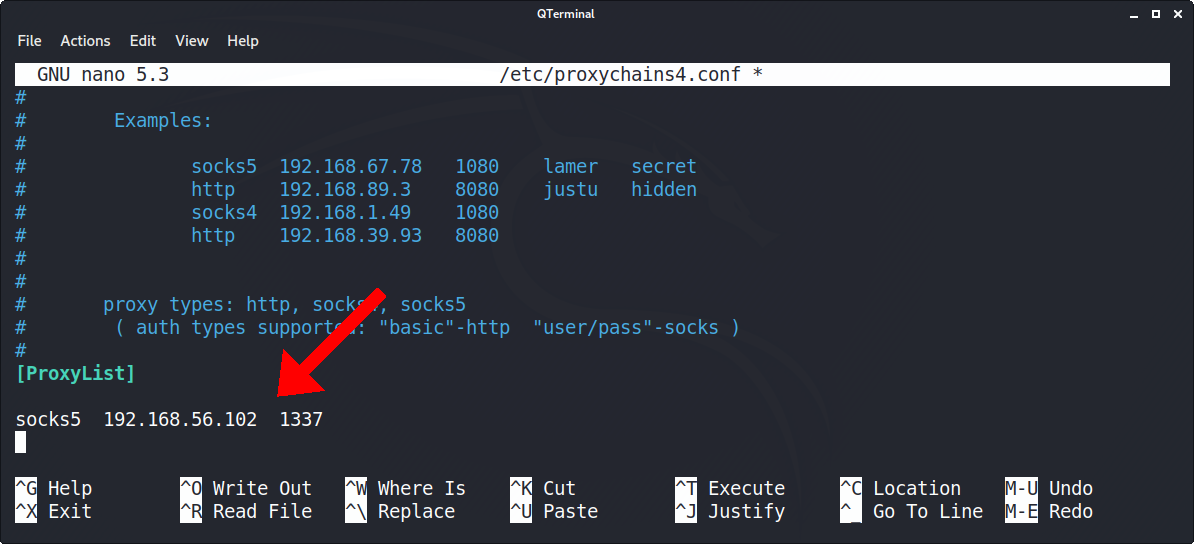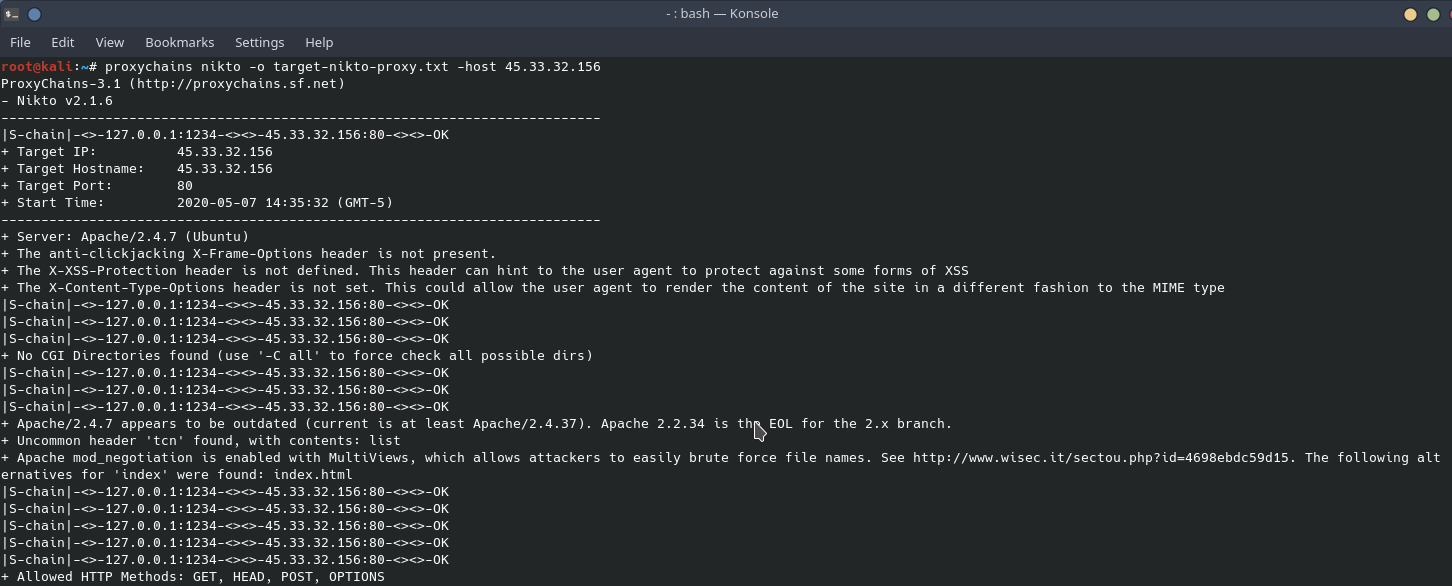
Offensive Security Guide to SSH Tunnels and Proxies | by Russel Van Tuyl | Posts By SpecterOps Team Members

Nmap-Vulners - NSE Script Using Some Well-Known Service To Provide Info On Vulnerabilities | Computer security, Machine learning deep learning, Internet skills